As cybersecurity comes to the fore, Microsoft Chief Security Advisor, Sarah Armstrong-Smith delved into the importance of zero trust at the itag AtlanTec Festival. The concept of zero trust does not automatically assume that people are the weakest link in cybersecurity. Rather, it is the key to securing the future of remote working. For Armstrong-Smith, the desire for more flexible working from any device at any time is supported and enabled by the zero trust principle.
At her talk, participants heard how most cyber attacks start with credential attacks. Multi-factor authentication and cloud infrastructure are just some ways that businesses can reduce their risk. Armstrong-Smith acknowledged that people are “creatures of habit” when it comes to password creation and this can lead to compromised usernames and passwords. However, we need to be empathetic to the changes brought about by remote working. Multi-factor authentication can go a long way towards bridging the security gap in this instance.
Within the cloud environment, the service provider assumes responsibility for the platform ensuring that business owners don’t have to worry about out-of-date unpatched servers. Companies were advised to look at what they have at present and to understand where the risk is. This shared responsibility model is one way industry can stay ahead of cyber criminals.
“People are not the weakest link, it is the process that is failing them,” said Armstrong-Smith at the itag AtlanTec Festival.
“Working remotely means there have been changes to procedures and to business models. We want to be productive and secure. Zero trust is not just about blocking, it’s about education. Attackers play to the psychology of people who are highly stressed and not thinking logically. Telling people not to click on a link is counter intuitive in the digital world. We need to take people on a journey – to have security embedded into everything we do. Set out what are the risks and what can we do from an education perspective.”
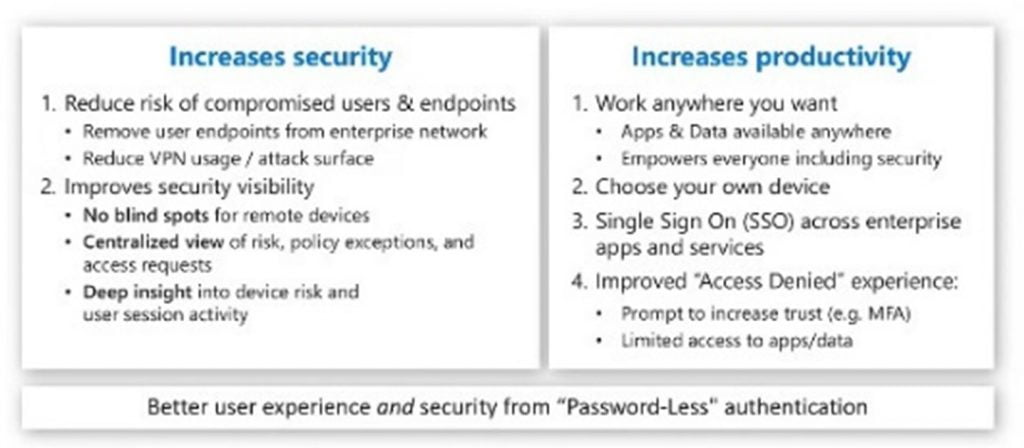
Trust Benefits Everyone
For zero trust to be successful, identifying patterns of behaviour is key. It is only when we know what normal behaviour is that we can identify abnormal behaviour. It is through this that security teams can discover anomalies. During her talk, she advised companies to look at the bigger picture rather than reacting to a single session. For Armstrong-Smith, zero trust is a dynamic concept which is constantly evolving. It is continual evaluation.
Living through a global pandemic has changed the risk profile and attackers are taking advantage. At the itag AtlanTec Festival, Armstrong-Smith pinpointed two key themes that are fundamental to cybersecurity and zero trust – identity and data. She described identity as the “glue” – advocating for one single identity to “manage and secure everything.” As she described, “the ability to control from the cloud is the glue that joins everything together.”
Zero trust has moved past the parameters of allow or deny. If abnormal user behaviour is found, companies can evaluate whether to allow access to some applications and services while restricting others. For example, the user may be able to view emails, but be prevented from downloading, printing and responding. The health of the user’s device is also important. Companies need to assess how the device is running, whether malware is present and how to react to that. Consideration must be given whether to block access, force an update or wipe the device completely, while being mindful of the user experience.
Remote working also has an impact on data sensitivity and protection. Armstrong-Smith advised participants at the itag AtlanTec Festival that the uploading of data into drop box and onto USB sticks is a chink in the armour. Participants also heard how companies must be mindful of internal threats to their organisation which has risen substantially over the last 12 to 18 months. Key indicators to look for could be poor performance reviews, redundancy or stress in the home environment. Education is the key to adopting zero trust principles. It is not just blocking but the ability to reaffirm why.